Small Package, Big Threat:
Wireless Network Attacks using Low-Power Embedded Devices
Wireless Network Attacks using Low-Power Embedded Devices
This was my final senior project at Western New England University. The project studies many new technological horizons in network security, wireless communications, and the "Internet of Things" of the future - Spring 2016.
General Idea
 Network security has always been a personal interest of mine. With the internet of things movement, billions of interconnected devices will be coming online in the next decade. Many of these devices are electromechanical systems that have the potential to be physically dangerous if a malicious user gains access. This project studies the current and future risks of network security utilizing small embedded devices that are available to a wide market. These devices will be used as a platform for penetration testing various network configurations and encryption types.
Network security has always been a personal interest of mine. With the internet of things movement, billions of interconnected devices will be coming online in the next decade. Many of these devices are electromechanical systems that have the potential to be physically dangerous if a malicious user gains access. This project studies the current and future risks of network security utilizing small embedded devices that are available to a wide market. These devices will be used as a platform for penetration testing various network configurations and encryption types.
Technology Requirements
There are many different options of single board computers to choose from for this type of project. Over the years, I have played around with the arduino (quite heavily), raspberry pi, beaglebone, various other Texas Instruments boards, and some of the one-off development kits you may have heard about like Chip.
I decided to go with the Beaglebone in part because I already had a couple from my previous development work, but also because it is (in my opinion) the best bang for your buck. It currently outperforms the raspi and has many more GPIO ports for the different peripherals you may want to connect to it down the road. The low power zigbee protocol was chosen due to it's open source nature compared to some of the other wireless techs like zwave.
Chapter 1
Problem In Society
The Internet of Things (IoT) phenomenon is putting billions of devices online in the next few years. It is estimated that by year 2020, over 20 billion interconnected devices will be online. Currently, digital security as a whole is perceived to be of low priority when designing technological systems and securing personal, business, or other enterprise solutions.
Traditionally, when someone wants to analyze a network for security vulnerabilities, a professional team of analysts would be hired to perform forensics. These professional penetration testers will come on-site to the physical location of the network and carry out various tests utilizing hundreds of different tools depending on the system and complexity of security requirements. This process has quite of bit of overhead and specialized skills associated with it, and therefore can be extremely expensive. Therefore, the barrier to entry for the general public to use these services is far too high. Homeowners and small business see no reason to do this. Unfortunately, this leaves a large portion of society vulnerable to security threats.
With traditional methods, a professional penetration tester would carry a laptop in his arsenal as the main platform for analyzing a network. The average laptop today can use about 60 Watts of power consumption while smaller embedded devices can use less than 2 Watts. Battery technology is a major priority with electronics getting even smaller year after year, and keeping consumption as low as possible with the best performance is vital to future computing platforms.
Commercial Applications
With the large overhead associated with hiring professionals to analyze networks, the hope for this project was to create a platform that could be marketed to penetration testers and security analysts to use in their arsenal of tools. This ultimately allows these professionals to pass on savings to their customers since they no longer need to physically be within a networks wireless distance, or monitor testing progress. This platform would also allow homeowners and small business owners to take matters into their own hands and actually test the network themselves if they wish to forego hiring out more expensive professionals. With less power consumption, this would also limit the cost associated with charging electronic devices so often.
Cyber Warfare is becoming a main part of military operations around the world. Having security platforms and devices in the field to defeat potentially dangerous hostile networks is, or will be, vital to military victory. This embedded device could be the base of such a platform in addition to a commercial solution.
Background Statistics
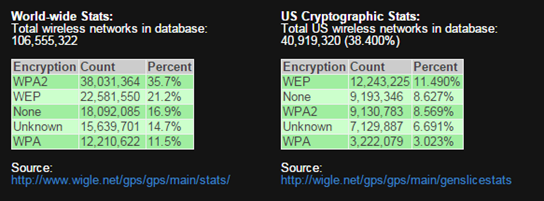
In 2013, a study shown in Figure 1.1 was done to illustrate the type of encryptions methods used to secure networks around the world and the U.S. Over 35% of the networks in the world used either no or very low security encryption types in 2013. 20% of the networks in the U.S. alone used either no or very low security encryption types. This percentage is far too high. The low security type of encryption used along with no security at all is WEP. Wired Equivalency Protocol or WEP, was created back in 1997 and later phased out in 2004 due to its incredibly insecure encryption algorithm. Yet, networks are still being setup and secured with WEP encryption.
Objective
The overall objective of the project was to successfully build a small form factor platform that could demonstrate how to defeat and secure a network. To prove viability, penetration of a low security environment would be carried out. More specifically, using wireless attacks to effectively disable a network with a WEP encryption protocol, which would simulate defeating over 35% of the world’s networks.
Criteria for Success
To consider this project a success, there were a few things that were desired to be accomplished. These included:
- The embedded device was to be physically comparable in size to an average smartphone (no more than 6” x 6” x 6”)
- The device uses no more than 5 Watts of power on average
- Device could be deployed remotely without any physical intervention after initiating an attack
- The device can wirelessly defeat a WEP encrypted network in a reasonable amount of time
Read the full report here...
Project Links
Hourly Breakdown
Full White Paper
DownloadPresentation Slide Deck
DownloadProject Team
-
- Alec Bewsee